Whenever an IAM user is created, it's best if it is tagged. The reason is simple... It gives more information about the user. One of the use-cases for user tagging could be to distinguish the user while running automation scripts. Various types of users are created. Some of the users are developers, some are a part of the DevOps team, some could be from the business team, some could be external devs, and the list goes on...
Note: Try to avoid creating IAM users as much as possible.
In this blog post, we will learn how to write an SCP that will enforce tagging of users with a specific key and value, while the user is being created.
What is SCP
According to AWS, SCP is:
Service control policies (SCPs) are a type of organization policy that you can use to manage permissions in your organization. SCPs offer central control over the maximum available permissions for all accounts in your organization. SCPs help you to ensure your accounts stay within your organization’s access control guidelines.
So basically an SCP is only available if you have enabled AWS Organizations. Using the SCP we can put a high-level policy that can allow or deny permissions to the AWS resources.
By default, when you enable AWS Organizations, a particular SCP is attached to the root account that will give full access to the AWS account. Since the SCP is attached to the root account, it will be applied to all the child accounts as well.
SCP vs IAM Policy
To understand the difference between SCP and IAM Policy, you can check out this article.
Only implementing SCP is not enough. IAM policy will have to be used for every IAM user/role or even group as per the requirements.
SCP to enforce tagging
Following SCP is used to enforce tagging. It makes sure that the IAM user is not created until a tag with the specific key value is present.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyCreateUserWithNoUserTypeTag",
"Effect": "Deny",
"Action": "iam:CreateUser",
"Resource": "*",
"Condition": {
"StringNotEquals": {
"iam:ResourceTag/userType": [
"SRE",
"Dev",
"Ext-Dev",
"Service"
]
}
}
}]
}
The above SCP states that the action iam:CreateUser which is used to create the IAM user will be denied if the user does not have a tag with the key userType and value from the following list of choices.
Apply SCP
In order to apply the above SCP, login into your AWS account and navigate to AWS Organizations (Make sure you're logging from the root account and you have AWS Organizations enabled)
Click on Policies
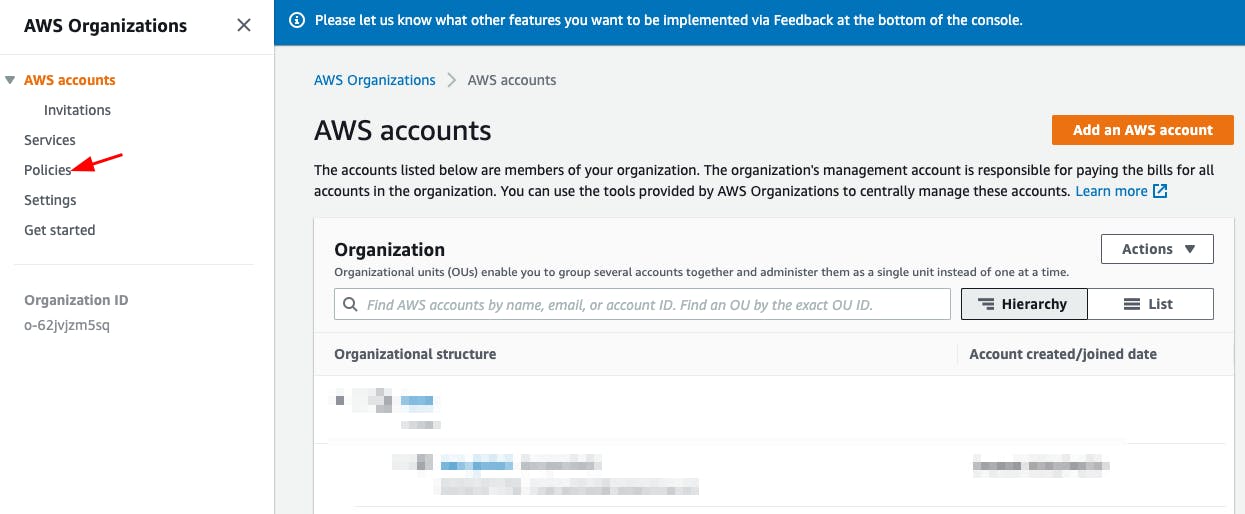
- Click on Service Control Policies (Make sure it is enabled)
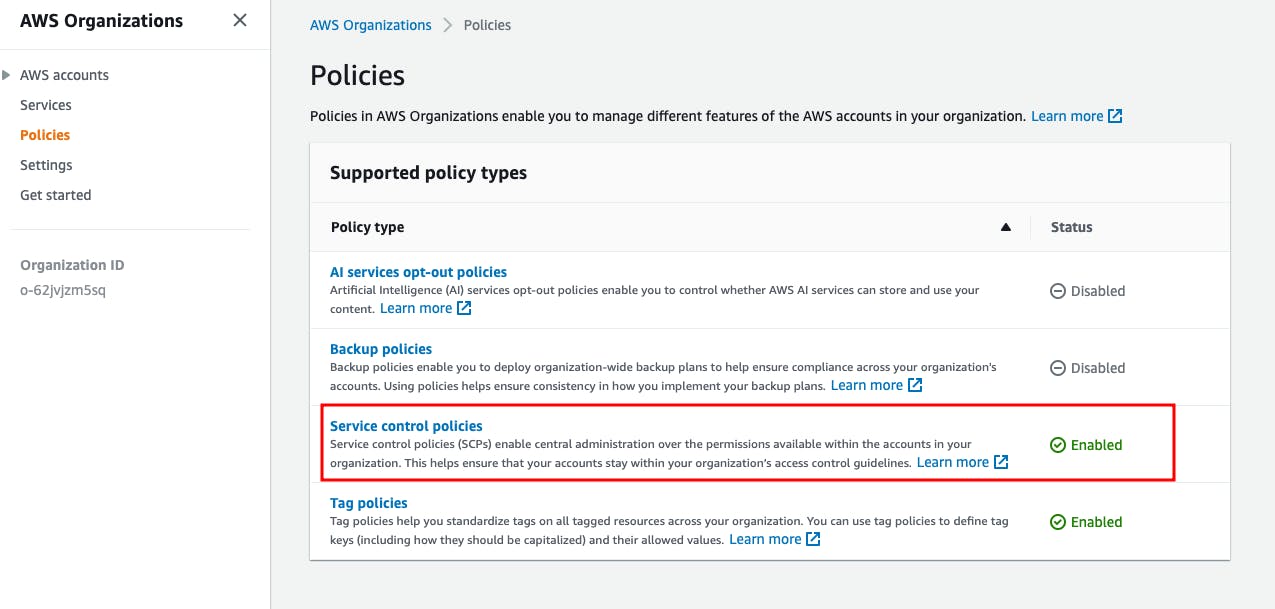
- Click on Create Policy and paste the policy in the edit field. Add name to the policy and description (optional)
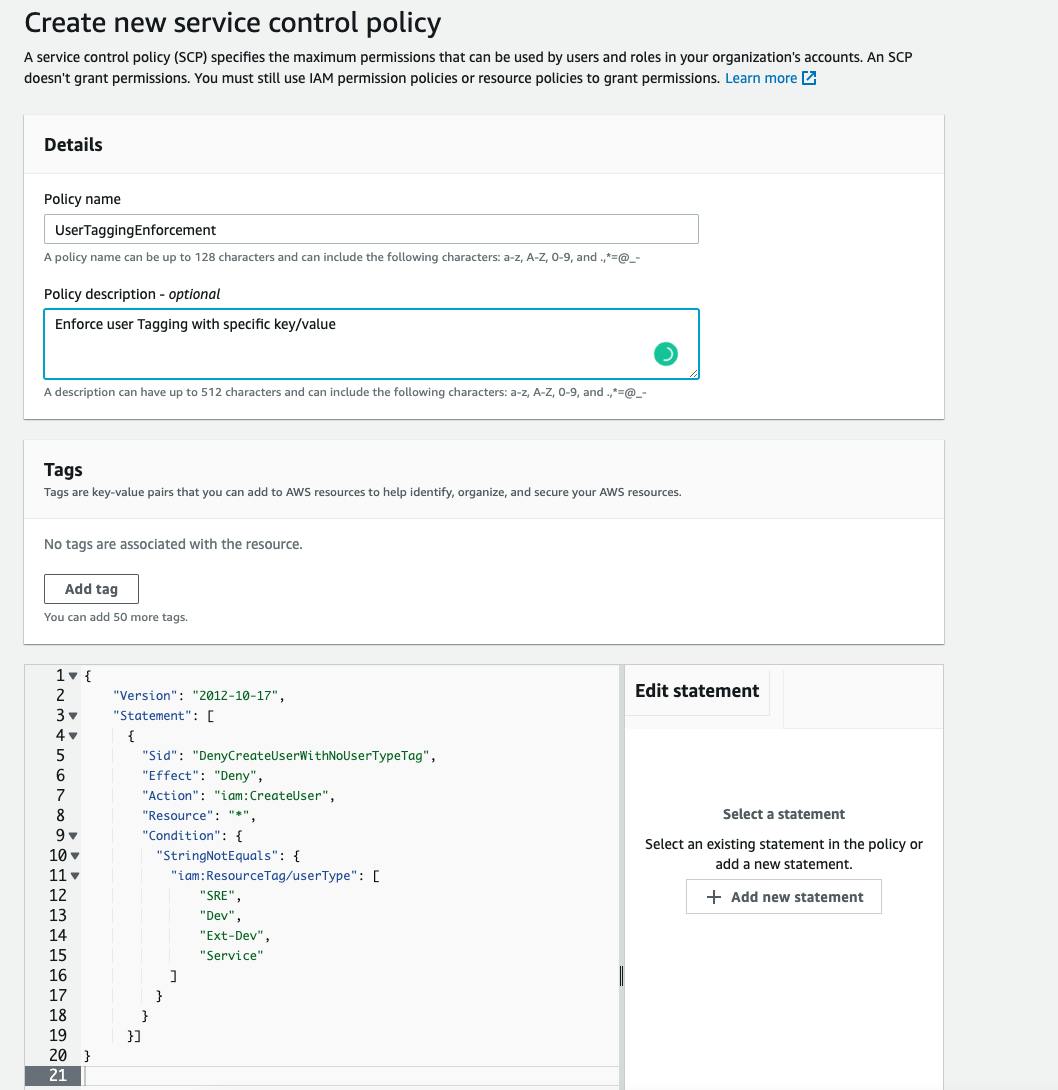
- Click on Create Policy. Now the policy is created. Next we have to attach the policy to the root account.
- Select the newly created policy and go to Targets tab. Click on Attach and select the root account.
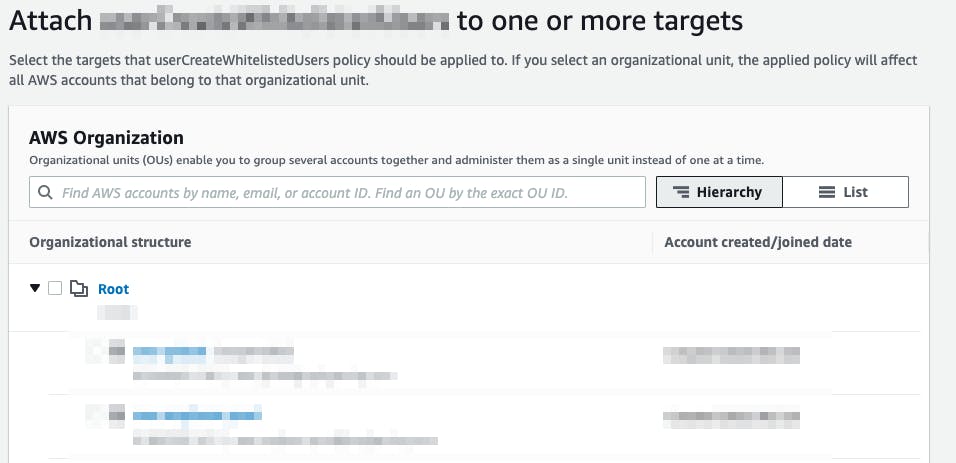
- Click on Attach Policy
Thats it! You have now attached an SCP that will enforce IAM user tagging while user creation. Go ahead and try creating an IAM user and check if the SCP is working as intended or not.
Conclusion
In this blog post, we made sure that whenever an IAM user is created there will be a tag attached to it that can be used for any automated or audit purposes.
You can use similar logic to enforce different SCPs. Share your ideas in the comment which SCPs do you enforce 🤝

